GitHub Bitbucket GitLab vulnerabilities
2019-05-04
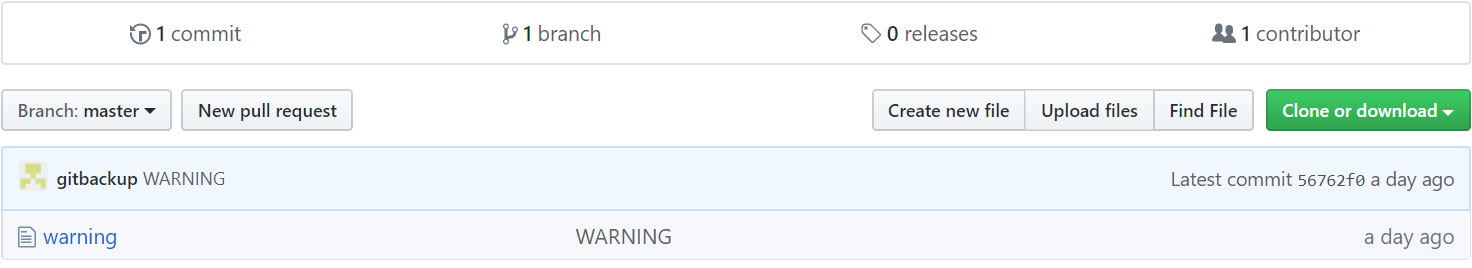
Hacker compromised hundreds of git accounts
The victims of the attack found their affected repositories empty. There was only one commit left with a file in which the hacker demanded payment of 0.1 Bitcoin.
Content of the file:
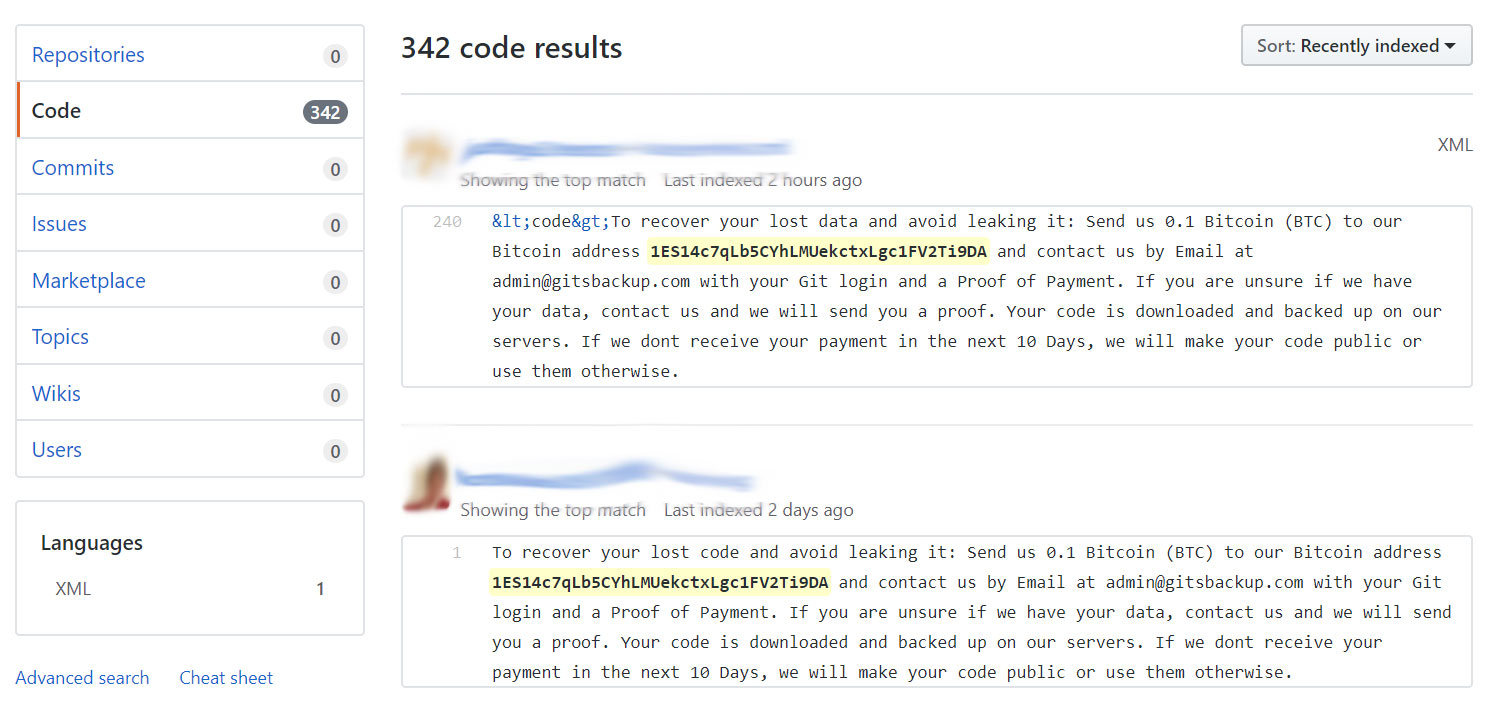
“To recover your lost code and avoid leaking it: Send us 0.1 Bitcoin (BTC) to our Bitcoin address ES14c7qLb5CYhLMUekctxLgc1FV2Ti9DA and contact us by Email at admin@gitsbackup.com with your Git login and a Proof of Payment. If you are unsure if we have your data, contact us and we will send you a proof. Your code is downloaded and backed up on our servers. If we dont receive your payment in the next 10 Days, we will make your code public or use them otherwise.”
A quick check of the mentioned Bitcoin Wallet 1ES14c7qLb5CYhLMUekctxLgc1FV2Ti9DA shows that it has not yet received any of the demanded 0.1 Bitcoin payments.
There is strong evidence of mass-scans of the affected files from the network 185.234.216.0/24.
It was also scanned for the following files:
/deployment-config.json
/.ftpconfig
/.remote-sync.json
/.vscode/ftp-sync.json
/.vscode/sftp.json
/sftp-config.json
/.idea/WebServers.xml
HUNDRESS OF THE AFFECTED ACCOUNTS
A search of the named wallet address on GitHub shows at least 342 affected accounts.
**GitLab's first statement showed that stored plaintext passwords could be the cause of the hack.**
“We identified the source based on a support ticket yesterday, and immediately began investigating the issue. We have identified affected user accounts and all of those users have been notified. As a result of our investigation, we have strong evidence that the compromised accounts have account passwords being stored in plaintext on a deployment of a related repository. We strongly encourage the use of password management tools to store passwords in a more secure manner, and enabling two-factor authentication wherever possible, both of which would have prevented this issue.”
Later this day an other offical statment was released
“GitHub has been thoroughly investigating these reports, together with the security teams of other affected companies, and has found no evidence GitHub.com or its authentication systems have been compromised. At this time, it appears that account credentials of some of our users have been compromised as a result of unknown third-party exposures. We are working with the affected users to secure and restore their accounts. We encourage all developers and customers to use two-factor authentication and strong and unique login passwords as a standard practice.”
Affected Bitbucket users got this information:
“Bitbucket Cloud Security Advisory: Unauthorized Access to your Repository
We are contacting you because your Bitbucket Cloud repository was recently accessed and deleted by an unauthorized third party. We are in the process of restoring your repository and expect it to be restored within the next 24 hours. We believe that this was part of a broader attack against several git hosting services, where repository contents were deleted and replaced with a note demanding the payment of ransom. During this attack, a third party accessed your repository by using the correct username and password for one of the users with permission to access your repository. We believe that these credentials may have been leaked through another service, as other git hosting services are experiencing a similar attack. We have not detected any other compromise of Bitbucket. We have proactively reset passwords for those compromised accounts to prevent further malicious activity. We will also work with law enforcement in any investigation that they pursue. We encourage you and your team members to reset all other passwords associated with your Bitbucket account. In addition, we recommend enabling 2FA on your Bitbucket account. If you have any questions or would like further assistance, please contact our support.
Sincerely, The Bitbucket Team”
WAYS TO RECOVER
The hacker did not delete the repositories as he claimed. He simply pushed a commit with the warning file to the head of the repository. Here are the steps to recover from the hack:
git checkout origin/master
git reflog # take the [SHA] of your last commit
git reset [SHA]If you have the latest files locally, this will fix everything:
git push origin HEAD:master --forceHOW TO PROTECT AGAINST THE HACK
First and foremost, immediately activate 2FA (Two Factor Authentication) in your Git account and then change your passwords and check for unkown users at your account. In a second step, we can block the git file on our web server.
For Apache 2.4
<DirectoryMatch "^/.*/\.git/">
Require all denied
</DirectoryMatch>For nginx
location ~ /.git/ {
deny all;
}For IIS
<configuration>
<system.webServer>
<security>
<requestFiltering>
<hiddenSegments>
<add segment=".git" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>HOW THE GIT HACK WORKED
It now seems pretty clear that the hacker simply scanned the Internet for public available /.git/config files. These files contain the remote paths and users have added usernames and passwords instead of using ssh keys.
After analyzing our own logs, we saw an increasing number of scans for /.git/config files. We even have strong evidence for the source network of the attacks. During the investigation we found some tools of @haxelt by internetwache which the attacker apparently used. These tools, already released in July 2015, can mass-scan for public available credentials in /.git/config files.
$ ./gitfinder.py -h
###########
# Finder is part of https://github.com/internetwache/GitTools
# Developed and maintained by @gehaxelt from @internetwache
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
usage: gitfinder.py [-h] [-i INPUTFILE] [-o OUTPUTFILE] [-t THREADS]
optional arguments:
-h, --help show this help message and exit
-i INPUTFILE, --inputfile INPUTFILE
input file
-o OUTPUTFILE, --outputfile OUTPUTFILE
output file
-t THREADS, --threads THREADS
threads